How to upgrade vRealize Orchestrator 7.4 to vRealize Orchestrator 7.5 or to be more precise… migrate! Since the release of vRealize Orchestrator 7.5 a couple of weeks ago the update/upgrade option with the vamicli and appliance management interface is not available (to my surprise).
A quick introduction to how I got in that situation: In my Home Lab my main vRealize Orchestrator appliance is running version 7.4.0 and is responsible for some day-to-day Orchestration of my multiple environments.
Here is the official VMware statement about the upgrade option in vRealize Orchestrator 7.5. It can be found in the vRealize Orchestrator 7.5 release notes:
You can no longer upgrade to the Orchestrator appliance 7.5, you can only migrate to it.
vRealize Orchestrator 7.5 – Release notes
For the people that are is still running way older versions
Environment
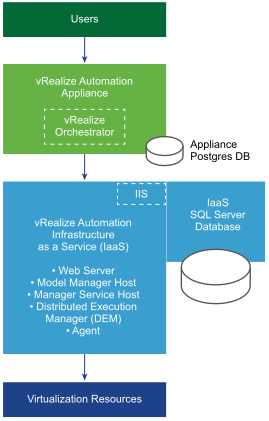
The following components were running in my environment and have been tested. Note: this part of my Lab environment is not running vRealize Automation. So I have not tested the migration with external vRO nodes in combination with vRealize Automation.
- A single vCenter Server 6.5.0 Update 2 (with an embedded PSC)
- A single vRealize Orchestrator 7.4.0 (external)
Scenarios
There are two options available. The first option is moving all data between the old and new vRealize Orchestrator. The second option is to migrate vRealize Orchestrator with the migration wizard. The second option is the one VMware recommends. The first option can be easier in some cases, some advantages are you retain your IP address, hostname and SSL certificates.
Both options are written down on this page.
vRO export data and redeploy
I have chosen for this scenario because this machine is only connected to a vCenter Server and can be reastablished very fast. Another reason is that the current vRO instance has been running since version vRO 7.0 and has been upgraded more than seven times in about 2.5 years. So a new clean install ain’t a bad thing!
Procedure:
- Create a package in the vRealize Orchestrator Client with all your created workflows, actions and resource elements.
- Save the package on a save place.
- Remove the registration from vCenter Server (if they are connected). Workflows “Unregister a vCenter Server extension” & “Remove a vCenter Server instance“.
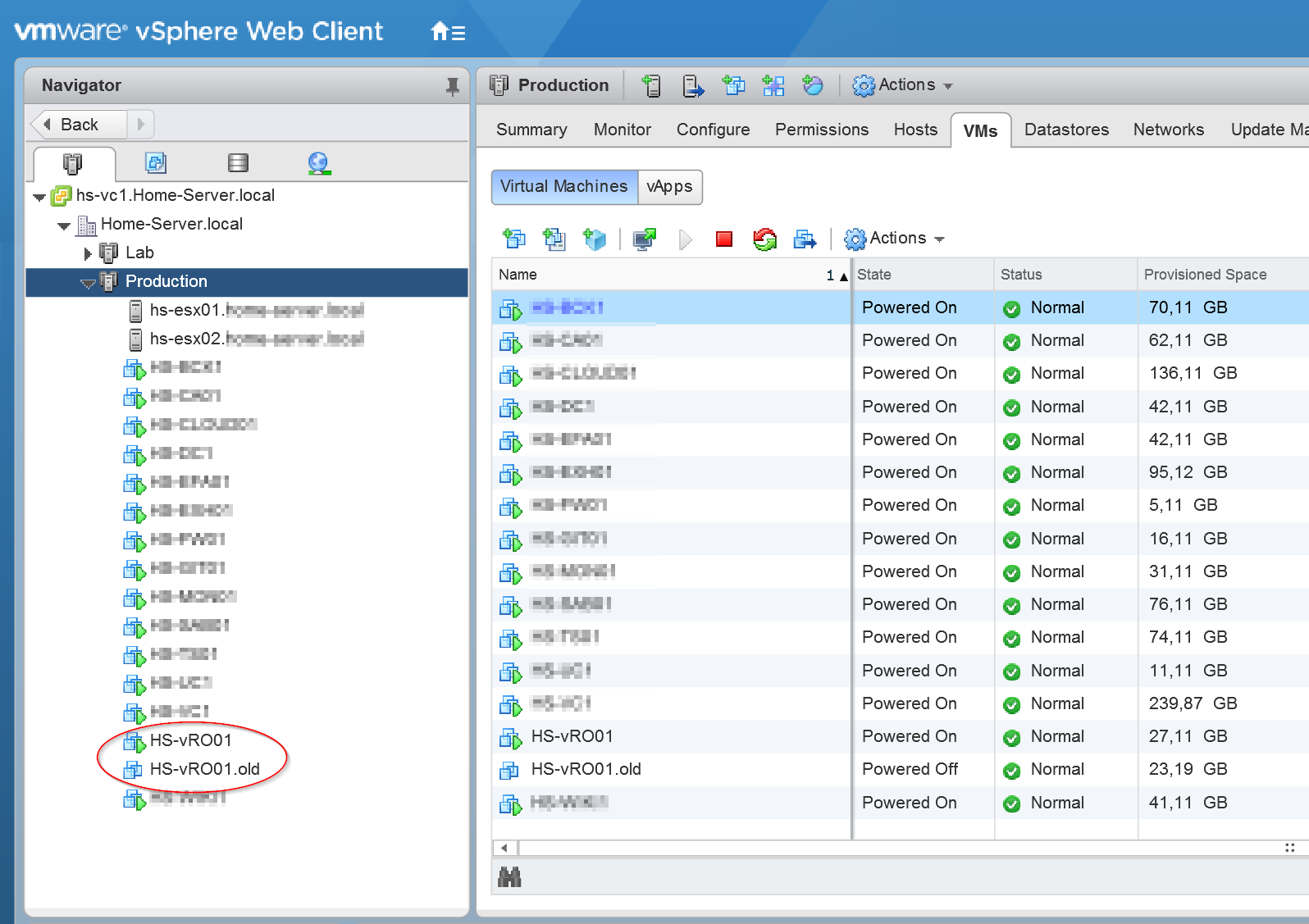
- Poweroff the current vRO appliance.
- Rename the appliance to %vm-name%.old (for example).
- Deploy a new vRealize Orchestrator Appliance on the same IP address and FQDN.
- Upgrade the virtual hardware.
- Walkthrough the vRealize Orchestrator configuration wizard.
- (Optional) install the SSL certificates.
- Import the package.
- Register with vCenter Server. Workflows “Add a vCenter Server instance” & “Register vCenter Orchestrator as a vCenter Server Extension“.
Screenshot(s):
vRO Migration
The migration path is performed in the following way (the official documentation is extensive, the link is listed below). The migration is a good option for an Orchestrator that is connected to a lot of extensibility and has a lot of plugins installed. The biggest issue for me was the new IP address, FQDN
Note: Migrations with vRealize Orchestrator Clusters are not described here. There are a couple of small items you need to check in the migration manual.
Prerequisites:
- Your source Orchestrator is running at least version 6.X.
- Make sure no workflows are running.
- Stop the Orchestrator services on the source Orchestrator.
- Make sure SSH is enabled on both the source and destination Orchestrator.
- Make sure no firewall is blocking traffic for the migration.
- Create backups from the source and destination Orchestrator.
Procedure:
- Register a new vRealize Orchestrator appliance in your IPAM solution.
- Deploy a new vRealize Orchestrator next to the currently running.
- Upgrade Virtual Machine Hardware
- Power-on the vRealize Orchestrator appliance.
- (Optional) Install new SSL Certificates.
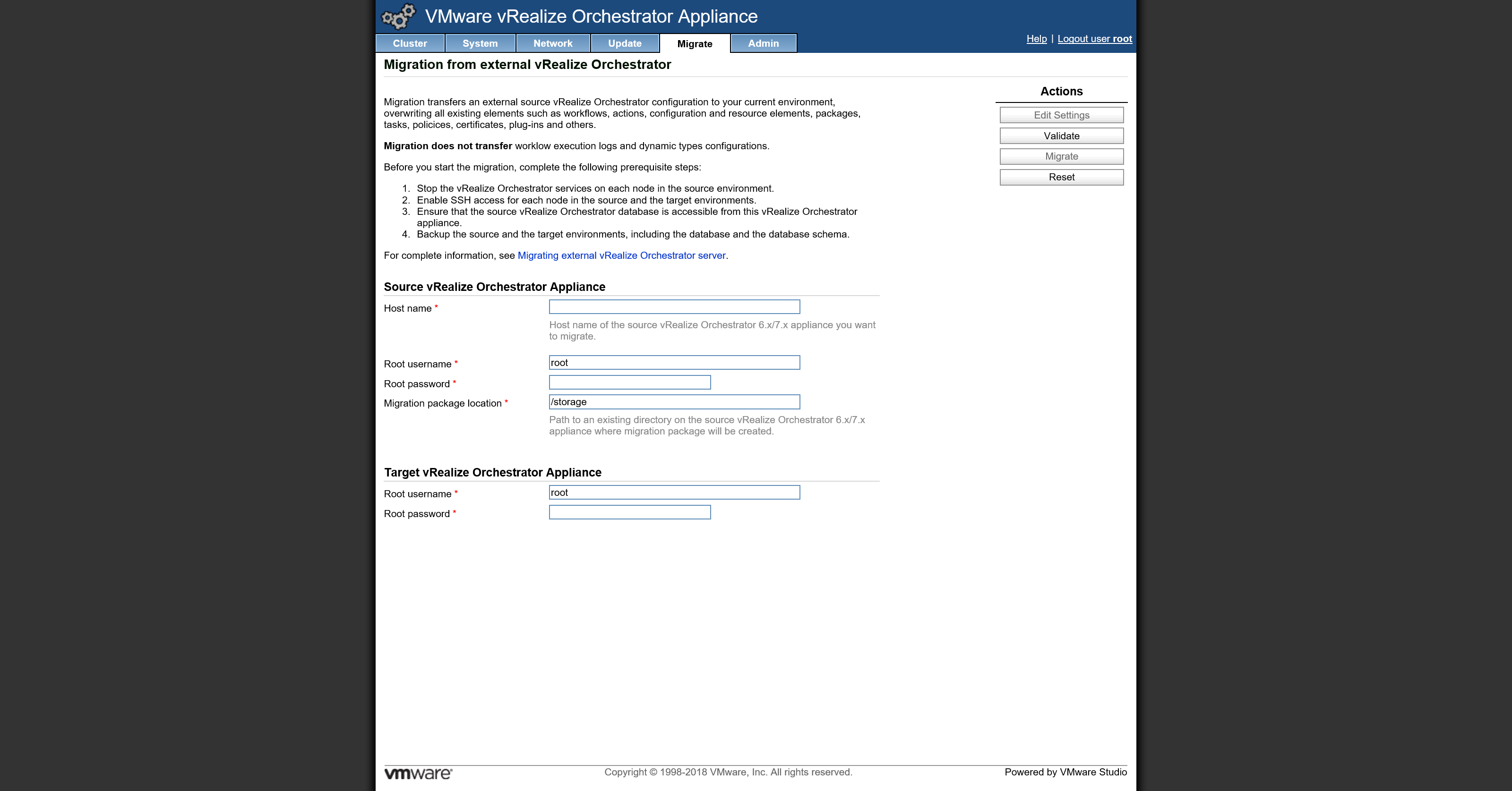
- Navigate with a browser to the Appliance Management interface (https://%FQDN%:5480).
- Login with the root credentials.
- Navigate to the migrate tab.
- Insert the required information.
- Start the validate and start the migration.
Source: Migrating vRealize Orchestrator – vRealize Orchestrator 7.5
Screenshot(s):
Note
Do not forget to configure and/or check the following items after a upgrade or migration:
- Timezone configuration (Appliance Mangement Interface)
- NTP server configuration (Appliance Management Interface)